Kong API Gateway
Overview
Kong is one of the most popular API gateways out there; but managing access to API and services behind it can be quite a bit of work especially as the application evolves requiring more and more advanced permissions models such as RBAC, ABAC & ReBAC.
With a recent update - Permit can now seamlessly integrate with Kong Gateway. And you can add permissions to your API within minutes without having to write a single line of code.
Connect your Kong Gateway to Permit.io
If you have Kong Gateway properly configured to relay requests from your users to your backend, you can easily use Permit.io to authorize requests as they go in, with a real time administration layer. This layer that has a nice user interface that is easy to understand for everybody in your organization, while still remaining policy-as-code behind the scenes.
Installing the PDP sidecar
Since Permit.io uses OPA internally, you can use the standard Kong OPA plugin.
This guide assumes that you already have Kong configured, and your authentication is done through Kong.
First, you will need to set up your Policy Decision Point, or PDP, next to your Kong Gateway. In the Permit.io architecture, the PDP is a small container that makes authorization decisions. You configure it through Permit.io's cloud service, but once it is running - it's completely independent (so it keeps running even if disconnected from the Internet) and can continue to make decisions extremely quickly, on the order of 1-5 ms.
To run the PDP, you can use the following command:
docker run \
-p 7766:7000 \
--env PDP_API_KEY=YOUR_PERMIT_API_KEY \
--env PDP_KONG_INTEGRATION=true \
permitio/pdp-v2:latest
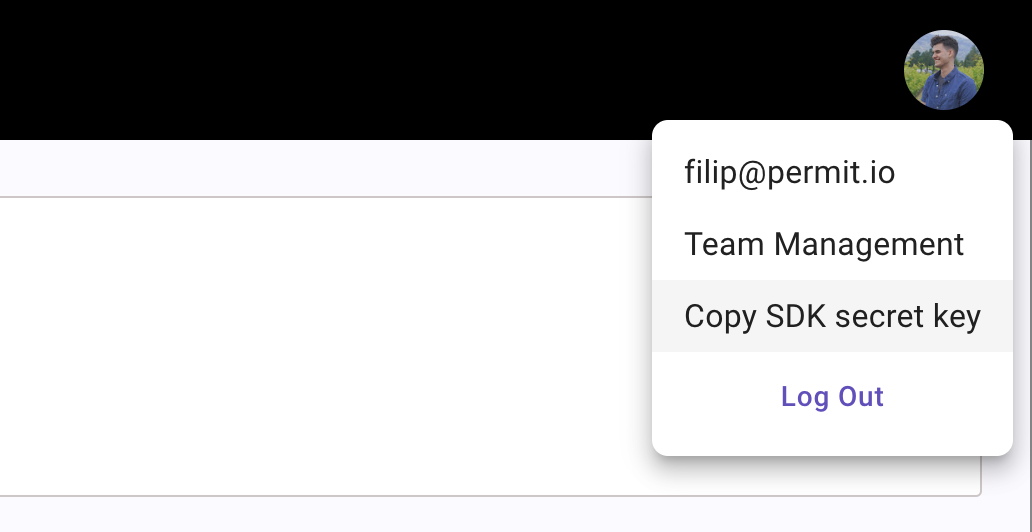
To get your API key, go to the Permit.io App and click “Copy SDK secret key” from your user profile.
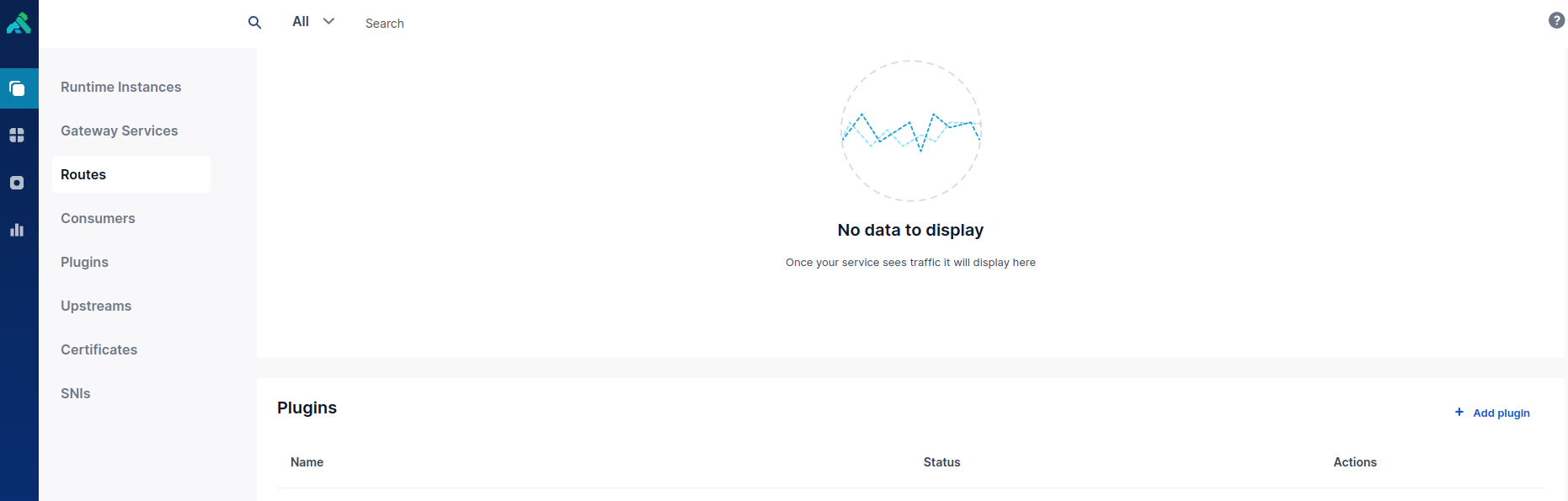
Adding the OPA plugin to Kong
Once the PDP container is running, you can configure your runtime instance to authorize requests through the PDP. In your Kong Route configuration, add a plugin. The option is located in the bottom right of the screenshot below.
If you changed any of the below values in the PDP configuration, they will need to be changed to match in the Kong's configuration as well.
In the plugin configuration, set the following values:
Consume OPA Input
Config.include Consumer In Opa Input - this should be checked.
Config.Opa Host
This is the PDP IP address - e.g. 192.168.60.231
Config.Opa Path
/kong
Config.Opa Port
7766
Config.Opa Protocol
http
Please use the image below for extra reference:

By default, / will be mapped to the "index" resource, and other routes to the first element in their paths.
/repo will be mapped to the repo resource.
Wrapping Up
Finally, go to the route you configured to see the outcome of the permission check.
As you see, Permit.io makes it easy to add permissions to Kong-based applications. You can easily configure Kong Gateway to use Permit's powerful permission engine to decide whether requests are allowed, and empower non technical people in your organization to manage permissions themselves.
For more information, such as how to customize the resource mapping table, see our blog post about Kong integration.