Audit Logs
Knowing who has done what in your application is critical for multiple reasons, including security, compliance, debugging and even just plain old monitoring. Audit Logs are a great way to track who did what, when they did it, why they had permissions and/or did not have permissions to do so!
They are a useful tool both for you and your team as the maintainers of your application, but also your end-users, who want to track their own usage and actions within the app.
Automatic Generation
As Permit.io powers your application, you are getting automatic audit logs.
Enforcement points, along with resource and action definitions, and user/tenant configurations automatically come together to generate the full picture needed for an audit log entry.
While the Permit web interface provides a dedicated page for viewing your audit logs, you can also find them directly in your deployed PDP microservice (as they are written to its stdout/stderr, you can of course stream them directly into your logging platform) .
Types of Audit Logs
There are two types of audit logs:
- Basic audit logs - these are the basic logs reflecting actions in regards to your policy rules.
- Decision logs - more in-depth logs reflecting "why" the policy engine made a decision.
View Audit Logs
Navigate to the Audit Log page in the Permit dashboard.
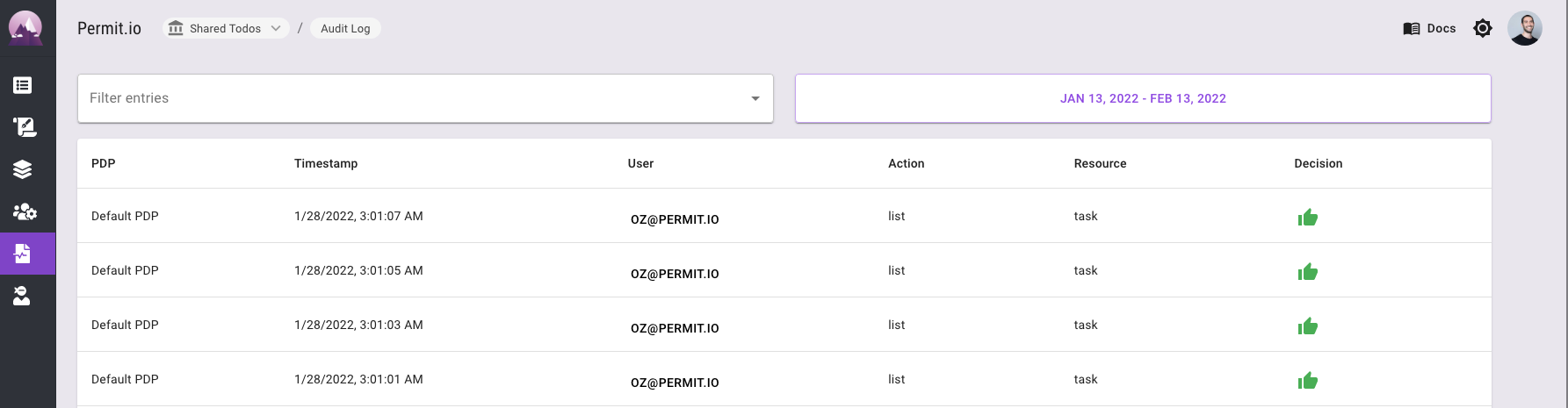
Above is an Audit Log example with 2 lines in which oz@permit.io asked to perform the actions list and delete on the resources task and document, following approval.
How to see more details about each Authorization decision?
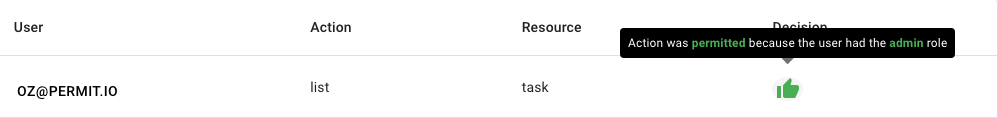
If you hover on the thumbs up icon under the decision column, you will see the reason the user is allowed or denied.
In the image below, oz@permit.io is allowed to list the task because he has the admin role.